Techniques for Protecting Private Visual Information
Just like me, there are millions of other people who utilize social media networks (e.g., Facebook, Instagram, Snapchat) on a daily basis. If we hold profiles on more than one social media network, we tend to share the same content across multiple platforms. Whether we post pictures, videos or statuses there are many ways our privacy can be intercepted on these platforms. Beyond privacy settings, do you really know who sees, saves, or scrapes this content? Images and videos can capture intimate memories, wandering bystanders in a park, or the beauty of nature. However, in these moments, we can also capture private visual information of ourselves or others.
Each year new social media networks rise to the forefront of technology. How will they ensure your privacy? What techniques will they implement to give their users peace of mind? We are developing eight mitigation techniques that can be implemented on any platform to protect your visual content.
At this point, you may be wondering…
“Why would I need these techniques? I know what privacy is and what information I should keep private.”
For Instance…
On social media networks, users share their triumphs, hardships, praises, and everything in between. Even though people can be thousands of miles away, our experiences ‘in the moment’ can be shared with many of our family members and close friends instantaneously. Below are a few examples of the typical pictures that are shared on social media networks.
Photo by Studio Reasons on Unsplash
New apartment leasers and homeowners tend to post pictures of their keys.
Images of keys can identify the maker, model, and potentially location.
Parents love to share their child’s life with many people around them.
Images of children can be exposed to dangers such as digital kidnapping and surveillance.
Every day, we share pieces of our lives with many other people, not only on social media but in-person as well. From colleagues at work to attendees at a party, we can capture these moments easily. Multiparty conflicts can arise when information is deemed to be private by a person in those images.
Photo by Kal Loftus on Unsplash
Images that have multiparty conflicts arise when another person did not permit to share the image on social media. These types of conflicts have the potential to damage reputation and even jobs.
If you find yourself posting these types of photos, then there may be room for a potential privacy leak. Don’t worry, millions of other people doing it with you. These types of images may not be identified as private like social security numbers and birth certificates, especially when it is openly shared on social media. Even though these in pictures the privacy concerns are not as prevalent, however, the user can be exposed to potential dangers.
Not only are typical users of social media networks exposing private information, but government agencies are exposing imperative information about employees and the organization. In January 2018, the Hawaii Emergency Agency posted this picture on their twitter. Not long after posting the image, it was removed because of the many privacy leaks (as seen below).

Fig 1. Hawaii Emergency Agency source: Twitter</
Note that one of the monitors display a post-it note with a password. This photo also exposes the location of the cameras which could lead to vandalism and burglary, a phone list which could lead to identity theft and harassment, and the badge of the employee which could lead to impersonation.
Mitigation Techniques
Given the various examples in which visual content can be exploited, we are building systems that will further help us understand those risks and mitigate them. Below are a few techniques we plan to implement:
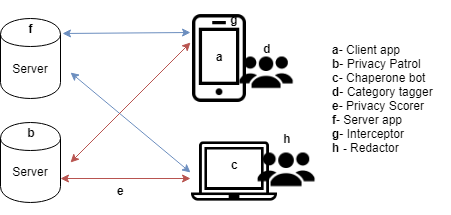
Fig 2. The location of each proposed mitigation technique.
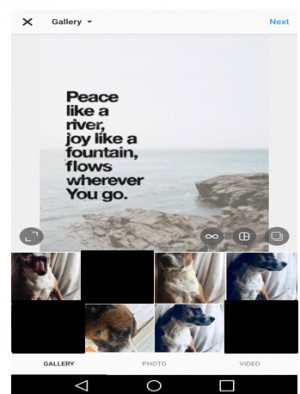
Interceptor (Figure 2g).
With the SMN applications, users will agree to let the SMN intercept the camera and gallery to flag and block content that should not be selected for posting.
In this example, several pictures from the user’s gallery are blocked because they are flagged to contain privacy leaks.
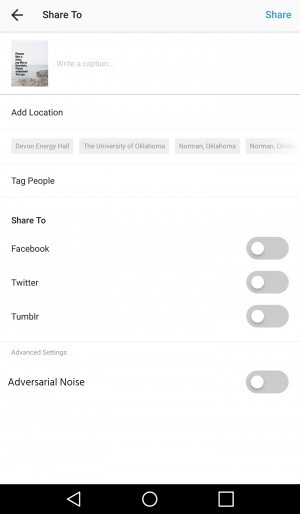 Redactor (Figure 2h).
Redactor (Figure 2h).
Using the SMN application, the users will be able to use redaction techniques to add secure distortions to visual content.
The redaction technique shown in this picture is adversarial noise (see the advanced settings). Adversarial noise adds an extra security layer which is focused on protecting the user from computer attacks.
Redaction Spectrum
Users may want to share images but hide other parts of their images. Web crawling systems may be collecting information for nefarious reasons. We propose a spectrum of techniques to obfuscate images from users or machines by using adversarial noise we prevent computers from seeing visual content which aids in safeguarding privacy.
Below is the full spectrum of features:
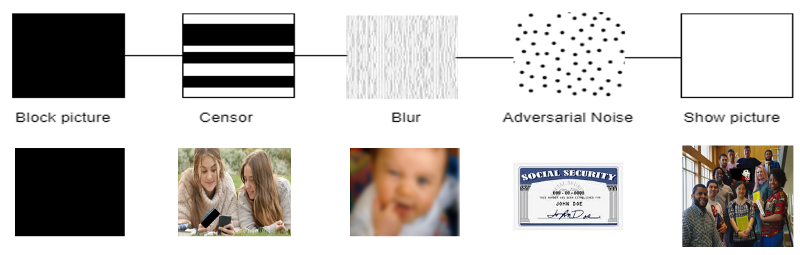
The system we are building encompasses these techniques and many more. Users will have the ease and accessibility of these techniques to customize their social media experience.
Modern censorship and privacy practices
Currently on social media, there are many practices these platforms use to protect users’ via profile settings and features. On platforms like Twitter and Facebook, users will see this type of censorship:
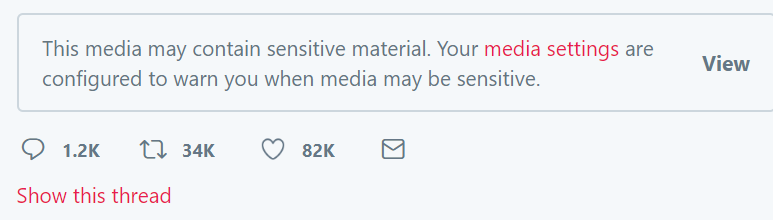
Depending on the flagged content from the viewer and the discretion of the poster, the visual content posted on social media will be censored by these types of techniques. It is our goal to make modern censorship customizable and flexible for users by implementing our mitigation techniques.
Steps toward a better privacy-based social environment start now! With the use of these proposed mitigation techniques, we can actively create a safer social media footprint for years to come. The personal and collective goal of the team members working and contributing to this project is to actively enhance the culture of social media networks and empower those who use these networks to reflect on their social media practices, actively engage with private leakage, and to enhance their knowledge of privacy.
If you are interested in learning more about this project or would like to volunteer to be apart of our collaborative research team, feel free to contact me at dehart.jasmine@ou.edu.
For updates and upcoming events, you can follow me (@jasdehart) and OU DALab (@oudatalab) on Twitter!


